Unlock Business Efficiency with Copilot Wave 2
Boost efficiency with Copilot Wave 2! Automate tasks, analyze data, and enhance collaboration—helping your business work smarter…
Boost efficiency with Copilot Wave 2! Automate tasks, analyze data, and enhance collaboration—helping your business work smarter…
The return-to-office debate is heating up—should your team go back full-time, stay remote, or find a middle ground? Here’s what every business should consider…
Think your backups are safe? Think again. Ransomware now targets outdated systems first, leaving businesses vulnerable to total data loss. Is your backup ready for the worst…

DIY tech solutions empower teams, but… without expert oversight, security risks, integration issues, and long-term maintenance challenges can emerge. Knowing when to get help is key…
Windows 11’s Start menu is getting smarter. Microsoft is fixing the frustrating Recommendations feature, making it more accurate and useful for daily workflows…
The right IT partner prevents issues, aligns tech with goals, and boosts success. If your current IT isn’t serving you, it’s time to explore your options…
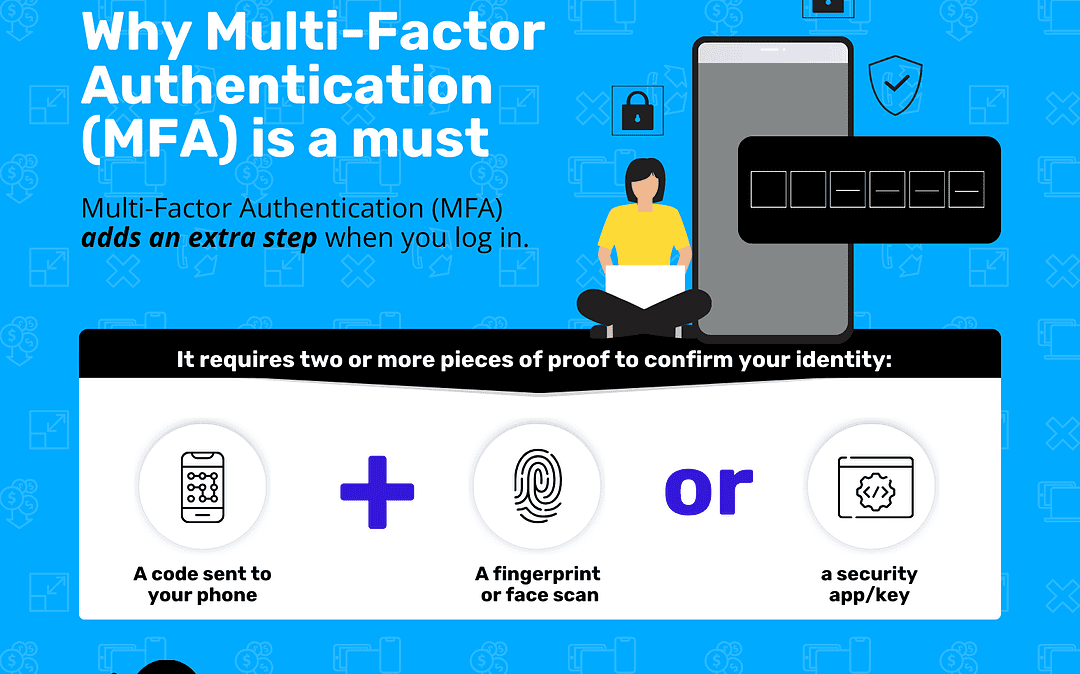
Cybercriminals are using corrupted Word files to bypass security and steal credentials. Always verify unexpected attachments, enable MFA, and train employees to spot phishing scams…
Chicago-area municipalities must modernize IT to enhance security, efficiency & citizen services. Learn how strategic IT solutions protect data & optimize operations by…